One of the most significant issues facing civil society and democracy activists has been how to use digital technology to assist their movements, writes Sana Kikhia, co-founder and executive director of the Sanad Group for Aid and Development. Often the approach is to treat these technologies as tools that promote democratic ideas and open societies. However, the experience of Syria show that just as important is the way of thinking that computer technology fosters, a mentality that can safeguard those working in an extremely hostile environment.
When the Syrian uprising began in 2011, people started organizing themselves using different tools. At that time, I co-founded a secret group within Syria to help Internal Displaced Persons (IDPs) across the country. Approaching this as a form of civil society activism, I came to realize that my background in network engineering- a CISCO networking certificate – influenced my management style. Unintentionally, I joined other activists in using computer theories to ensure our safety and effectiveness.
 Protection techniques are vital in a country like Syria, where even before the uprising, we learned that we could not do anything without the blessing of “the fear state.” The current regime is built on and rules through fear. We broke this rule when we first called for freedom – a demand which cost many people their lives. State repression caused the internal displacement of many thousands, as the regime sought out activists, forcing them to leave home. The Syrian regime targeted others as “traitors,” forcing them to abandon their homes, simply because pro-democracy demonstrations had occurred in their neighbourhoods. Then the regime started persecuting those who provided humanitarian aid or assisted the displaced families.
Protection techniques are vital in a country like Syria, where even before the uprising, we learned that we could not do anything without the blessing of “the fear state.” The current regime is built on and rules through fear. We broke this rule when we first called for freedom – a demand which cost many people their lives. State repression caused the internal displacement of many thousands, as the regime sought out activists, forcing them to leave home. The Syrian regime targeted others as “traitors,” forcing them to abandon their homes, simply because pro-democracy demonstrations had occurred in their neighbourhoods. Then the regime started persecuting those who provided humanitarian aid or assisted the displaced families.
We began our volunteer group for non-political, humanitarian reasons. We acted as our humanity urged us to do, to help the most vulnerable displaced people. In the spirit of a democratic uprising, we did not wait for the state to give us permission or blessing. We decided not to register, knowing that at best the regime would either arrest us or force us to help its supporters. We mainly offered in-kind support and covered some expenses for IDPs in half of Syria’s 14 provinces. Officially registered charities ignored many displaced Syrians, precisely those who needed help. To avoid state detection, we did not publicly disclose the details of our work. We did not even tell the families we were supporting about Sanad or about our identities, just that we were helping them regardless of their backgrounds.
We started communicating through secret social media groups as we needed to protect aid recipients and ourselves. Incorporating new activists into our group was difficult as there was a risk that they could be regime informants. However, we created what was in effect a vouching system in which any member could add a friend to the group as long as they fully trusted that person. In turn, the new arrival could add another trusted person. The result was the group grew steadily even though we did not know the real names of most of the other members. We became like a spider’s web, linked by human nodes.
Such practices allowed us to build a robust network, but we had a significant vulnerability. There was a danger that the regime would arrest and torture one of us, forcing the victim to reveal our group’s existence of and some of the members’ real names.
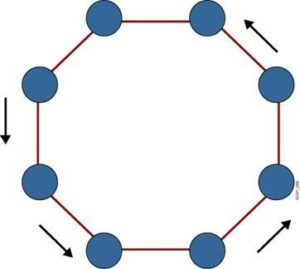 To protect ourselves from this risk, we built a new form of network similar to those used by computers. Over the years, computer networks gradually developed by linking two devices together and then adding more to form a ring (“Ring topology” – right).
To protect ourselves from this risk, we built a new form of network similar to those used by computers. Over the years, computer networks gradually developed by linking two devices together and then adding more to form a ring (“Ring topology” – right).
Such “ring topology,” as it is known, turned out to be very risky. Although each node is only connected to two other nodes, if you lose one node that will break the loop and break the connection. This was the same with some Syrian activist groups, which the regime could paralyze by capturing one volunteer. Although that person could at most give information about two others, the group would stop functioning. In addition to people being forced to divulge information under torture, the other risk we had to reduce was the regime’s extensive network of informers. Since the 1970s the Syrian regime had created a web of informers throughout the country, inside workplaces, universities, schools, neighborhoods, and families. A son might report his parents if they acted against the regime, which of course could mean something as minor as an offhand comment.
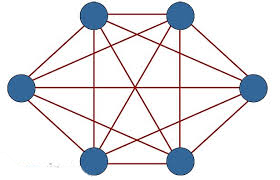 To further protect ourselves, we adopted a network approach similar to “mesh topology.” In the “mesh” approach, each node is connected with every other node – what we could call ‘’the social life of computers networks.’’ Through such “distributed communications,” transmissions are maintained even if one connection is broken (“full- mesh topology” – left).
To further protect ourselves, we adopted a network approach similar to “mesh topology.” In the “mesh” approach, each node is connected with every other node – what we could call ‘’the social life of computers networks.’’ Through such “distributed communications,” transmissions are maintained even if one connection is broken (“full- mesh topology” – left).
The difficulty with the mesh approach is that what works to reduce risks for computers can create dangers for activists. Mesh topology means that if one node fails, communications continue. In the Syrian context, however, each node represents a person who under torture can reveal communications with all the other nodes, leading to catastrophic failure. We therefore adopted a modified version of “mesh topology” (see graphic, Syrian partial- mesh topology).
Our partial- mesh topology created different classes of nodes. Most were only partially connected to the network. They were only connected to those with whom they exchanged data, such as volunteers working on the same project. This reduced the risk that one node would put all the others in danger. Of course, this could limit communication as you could not rely on all the nodes to deliver a signal. However, this is a price worth paying. A few nodes – such as my social media profile – were connected to all the others.
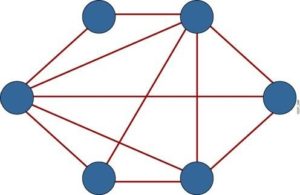 The practical impact of the partial- mesh approach was significant. Take the example of delivering medicine to an area under pressure from the regime’s security forces. This mission was like a computer signal, which our network would distribute in different forms to different nodes. A few volunteers would take responsibility for delivering the medicine, while others would undertake other aspects of the mission or take responsibility for reporting problems. The mission, like a computer signal, would hop from node to node or in this case from volunteer to volunteer, until it reached its destination. Multiple people ensured the medicine reached the IDPs with minimal risk.
The practical impact of the partial- mesh approach was significant. Take the example of delivering medicine to an area under pressure from the regime’s security forces. This mission was like a computer signal, which our network would distribute in different forms to different nodes. A few volunteers would take responsibility for delivering the medicine, while others would undertake other aspects of the mission or take responsibility for reporting problems. The mission, like a computer signal, would hop from node to node or in this case from volunteer to volunteer, until it reached its destination. Multiple people ensured the medicine reached the IDPs with minimal risk.
We excluded those nodes or volunteers which we did not need in order to reduce the number of people exposed to danger. We did not meet in person, exchange real contact details, or use real names. The result was a network that was very reliable and, when damaged, was self-healing. As we could not expect anybody under torture to keep secrets, it was safer not to share unnecessary information such as the existence of other nodes. When the security forces capture a volunteer, they cannot give up the details of all the other nodes and, in any case, they know very few, if any, of their real names. The Syrian partial-mesh also helped with recruitment. New members felt safer joining a group in which names did not matter and which did not demand personal details.
The Syrian partial-mesh also created redundancy. We always needed at least two people to be aware of an activity. If the regime arrested one volunteer, the backup would know where, when, and with whom the detained person was supposed to have met, for example. The back-up volunteer could safeguard the contact by warning them.
Of course, the creation of the Syrian partial-mesh was also a result of the international failure to safeguard activists and humanitarian aid workers. The Syrian regime and its allies have deliberately attacked those who international humanitarian law is supposed to protect. There has been no meaningful international response. In the end, were we able to defend ourselves by using techniques from computer networking.







